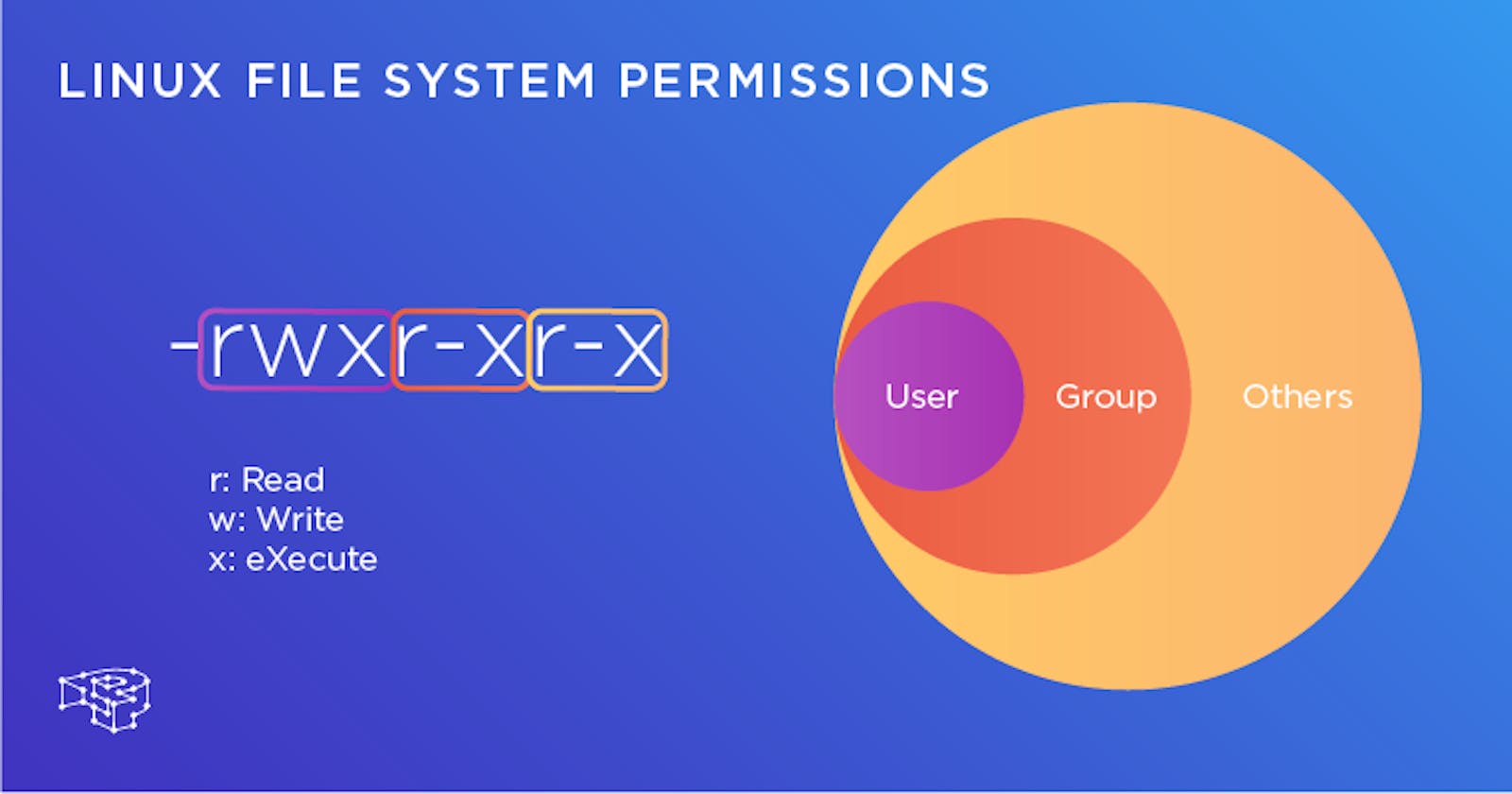
In Linux, file permissions play a crucial role in ensuring the security and integrity of the system. Every file and directory on a Linux system has a set of permissions that determine who can access the file, and what actions they can perform on it. In this article, we'll discuss the basics of file permissions in Linux and how they can be used to secure your system.
In Linux, file permissions can be represented using three digits or numbers: owner permissions, group permissions, and others permissions. Each digit represents a combination of read, write, and execute permissions.
Here's a breakdown of the digits and their corresponding permissions:
0: No permission. The user cannot read, write, or execute the file.
1: Execute permission. The user can execute the file, but cannot read or write to it.
2: Write permission. The user can write to the file, but cannot read or execute it.
3: Write and execute permissions. The user can write to and execute the file, but cannot read it.
4: Read permission. The user can read the file, but cannot write to or execute it.
5: Read and execute permissions. The user can read and execute the file, but cannot write to it.
6: Read and write permissions. The user can read and write to the file, but cannot execute it.
7: Read, write, and execute permissions. The user can read, write, and execute the file.
For example, if a file has the permission "755", it means that the owner of the file has read, write, and execute permissions, while the group and others have only execute and read permissions. If a directory has the permissions "644", it means that the owner can read and write to the directory, while the group and others can only read the directory.
To view the permissions of a file or directory, you can use the ls -l command in the terminal. The output will show the file/directory name, followed by the owner, group, size, and permission string. For example:
-rw-r--r-- 1 user group 22 May 15 10:00 myfile.txt drwxr-xr-x 2 user group 4096 May 15 10:01 mydirectory
The first character in the permission string indicates the type of file - "d" for directories and "-" for regular files. The next nine characters indicate the permissions for the owner, group, and others in groups of three.
ACCESS CONTROL LIST
ACL (Access Control Lists) in Linux is a way to provide more detailed and fine-grained control over file and directory permissions. While standard file permissions (read, write, execute) determine access based on user, group, and others, ACLs allow you to set permissions for specific users or groups beyond the standard categories.
Here's an example that demonstrates the usage of ACL in Linux:
Let's say you have a directory named "shared_folder" that is used by multiple teams in your organization. You want to provide different access levels to each team.
Create the shared folder:
$ mkdir shared_folderSet the default permissions:
$ chmod 770 shared_folderThis command sets the default permissions to read, write, and execute for the owner and group, and no permissions for others.
Add ACL entries for specific teams:
$ setfacl -m u:marketing:rwx shared_folder $ setfacl -m g:sales:rx shared_folder $ setfacl -m g:development:r shared_folderThe above commands add ACL entries for different teams:
The marketing team (user: marketing) has read, write, and execute permissions.
The sales team (group: sales) has read and execute permissions.
The development team (group: development) has read-only permissions.
$ getfacl shared_folderRunning the "getfacl" command displays the ACL entries for the shared folder, including the default permissions and the additional ACL permissions.
Test the access:
If you log in as a member of the marketing team, you will have full access to the shared folder directory.
If you log in as a member of the sales team, you will have read and execute access to the shared_folder directory.
If you log in as a member of the development team, you will have read-only access to the shared folder directory.
Other users who don't belong to any of the specified teams will have no access to the shared_folder directory.